Enterprise Use Cases
Learn how Red Kite EASM can support your organization.
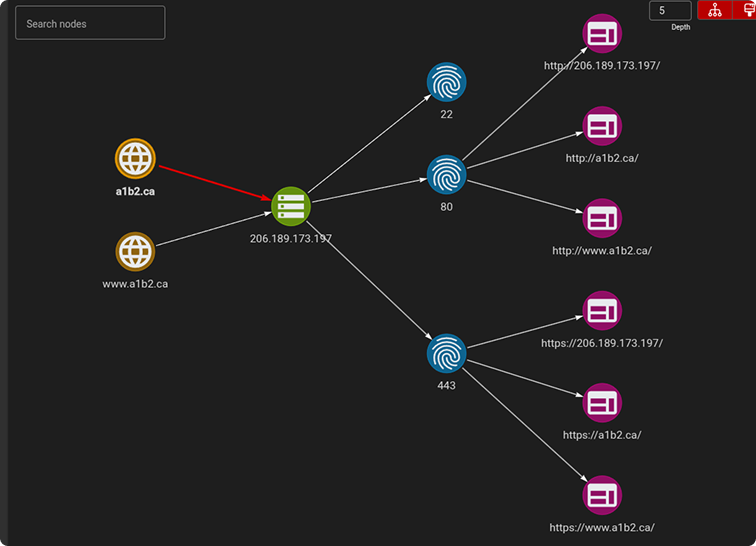
Support and empower manual testing
Leverage your existing investments in cybersecurity experts
Give your testers the tools and visibility they need to work smarter, not harder.
- Speed up reconnaissance
- See the big picture, then explore specifics.
- Turn analyst insights into repeatable test cases
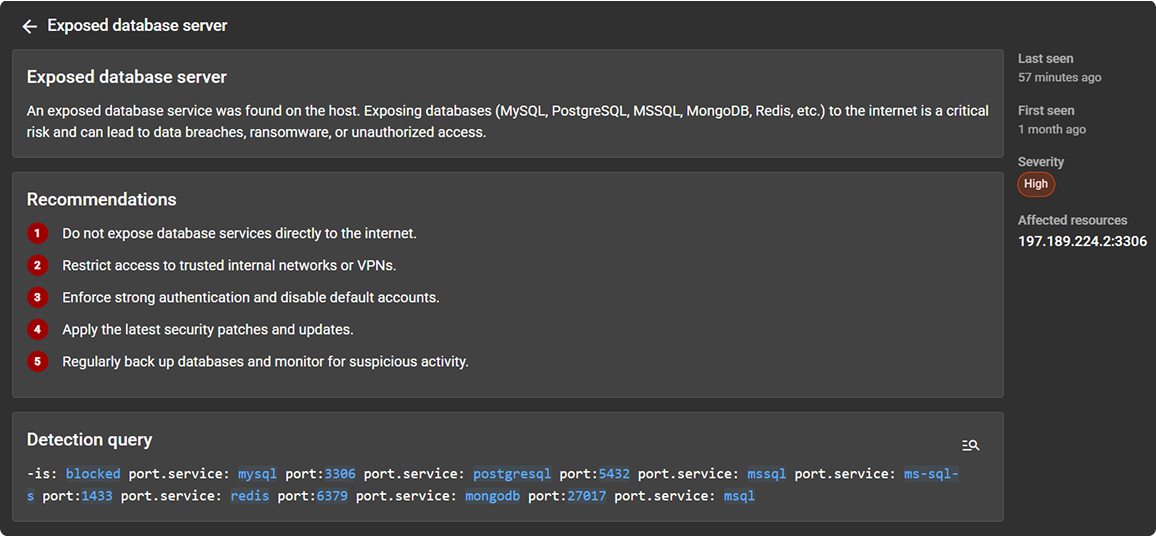
Identify shadow IT
Spotlight new and unknown attack surface
Highlight shadow IT and unmanaged services that bypass official inventories.
- Discover unknown assets
- Prioritize risky findings
- View recent attack-surface changes to focus on new threats
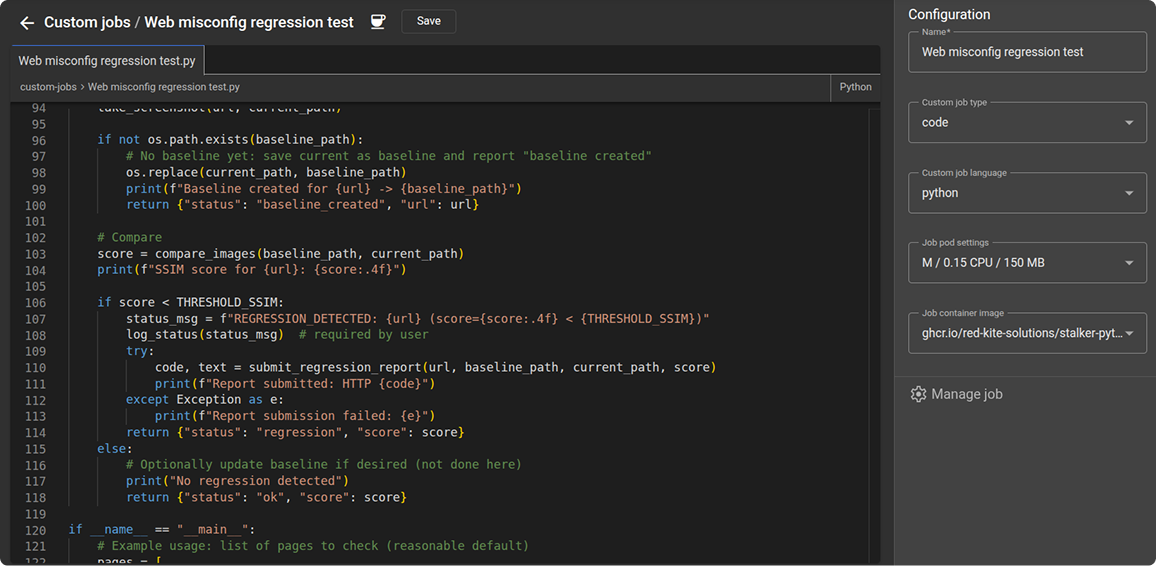
Perform regression testing on your infrastructure
Prevent known issues from harming you again
Automate recurring checks to maintain a consistent security baseline.
- Automate recurring checks
- Detect deviations before impact
- Reduce firefighting efforts
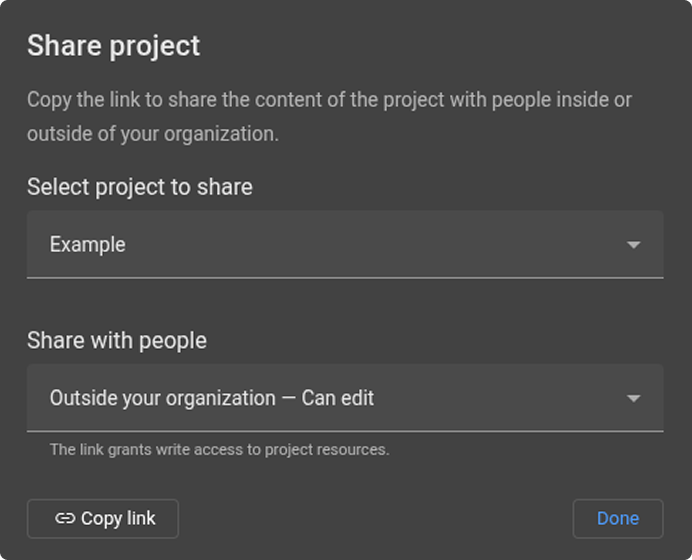
Collaborate between teams
Break the silos
Ensure security operations, vulnerability management, offensive security and engineering collaborate effectively.
- Share just enough data with just the right people
- Ensure knowledge transfers across teams
- Prevent redundant efforts
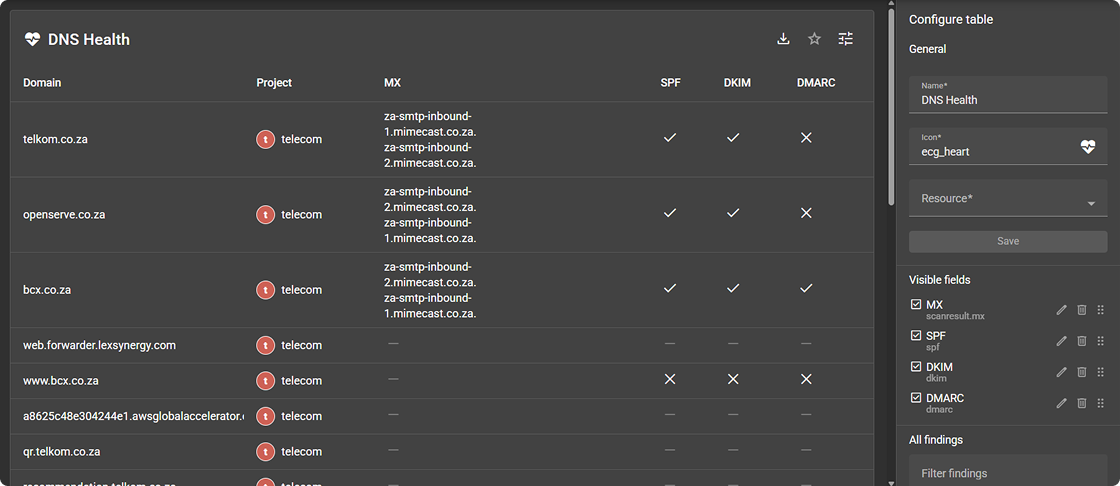
Customize your views
Focus on what matters to you
Tailor dashboards and reports to highlight what matters.
- Save personalized views
- Share view with stakeholders
- Adapt reporting